The war that could trigger World War III likely won’t start with missiles. It won’t begin with invasion broadcasts or synchronized military movements. Instead, it may start at 2:47 AM on a Tuesday, in a network operations center somewhere, when operators lose communications with a power generation station that supplies electricity to 15 million people. And by the time system administrators realize they’ve been attacked, the damage will already be irreversible.
This is not speculation. This is the most probable first move in any conflict between NATO and Russia or between the United States and China, according to the U.S. Director of National Intelligence 2025 Threat Assessment, NATO cyber officials, and every advanced cyber threat analysis published in 2025. The only uncertainty is not whether such an attack will occur—it’s when, where, and whether NATO’s Article 5 collective defense clause will be invoked to justify military retaliation.
The core tension is stark:
- Capability Exists: Russia’s Sandworm group has successfully compromised power grids and demonstrated kill chain execution capabilities in Ukraine’s grid, attacking 1,000+ times since 2022
- Vulnerabilities Cascade: Power grids contain 50+ critical vulnerabilities with CVSS scores of 9.8-10 (maximum severity), many unfixed and unpatched across Europe and North America
- Dwell Time Extreme: Attackers average 200+ days inside target networks before detection, meaning pre-positioning for attacks has likely already begun
Cyber Power Grid Attack Kill Chain: Stages, Detection Difficulty, and Timeline
- Escalation Ambiguity: NATO has no defined threshold for when cyber attacks trigger Article 5—creating strategic uncertainty that could either deter or accidentally trigger nuclear escalation
This analysis examines the technical reality of cyber warfare against power grids, the military actors preparing such attacks, and the terrifying gap between defensive capability and the sophistication of the threat.
Why 2025 Is the Year Cyber Warfare Becomes Reality
The Ukraine Laboratory: Proof of Concept
Between March and August 2024, Russia conducted nine large-scale coordinated attacks on Ukraine’s power grid, launching over 1,000 individual strikes throughout 2024-2025. These were not espionage operations or low-intensity probing. They were deliberate, kinetic-scale destruction campaigns designed to inflict maximum suffering on civilian populations during winter.
Key data points from the Ukraine campaign:
Scale: Russia damaged three times more power generation capacity in 2024 than in the previous winter of 2022-2023. One major energy company reported that 2024 attacks damaged equipment exceeding the cumulative damage from 2022-2023 combined.
Geographic Reach: Attacks struck critical infrastructure in 20 of 24 Ukrainian regions, demonstrating Russia’s ability to maintain geographically dispersed targeting capability.
Persistence: Despite Ukraine deploying U.S. Patriot systems, NATO air defense, and hardened cyber protection, Russian attacks continued at undiminished intensity. Ukraine’s air defense success rates for drones have fallen to 80% by October 2025—unsustainable economics where each interceptor costs millions while each drone costs $20,000.
Cyber-Kinetic Integration: Russia coordinated cyber operations with traditional missiles and drones, demonstrating it can layer attacks through both channels simultaneously—a capability NATO planners assess could be deployed against European targets.
Sandworm APT Evolution: 10 Years of Escalating Cyber Power Grid Attacks (2015-2025)
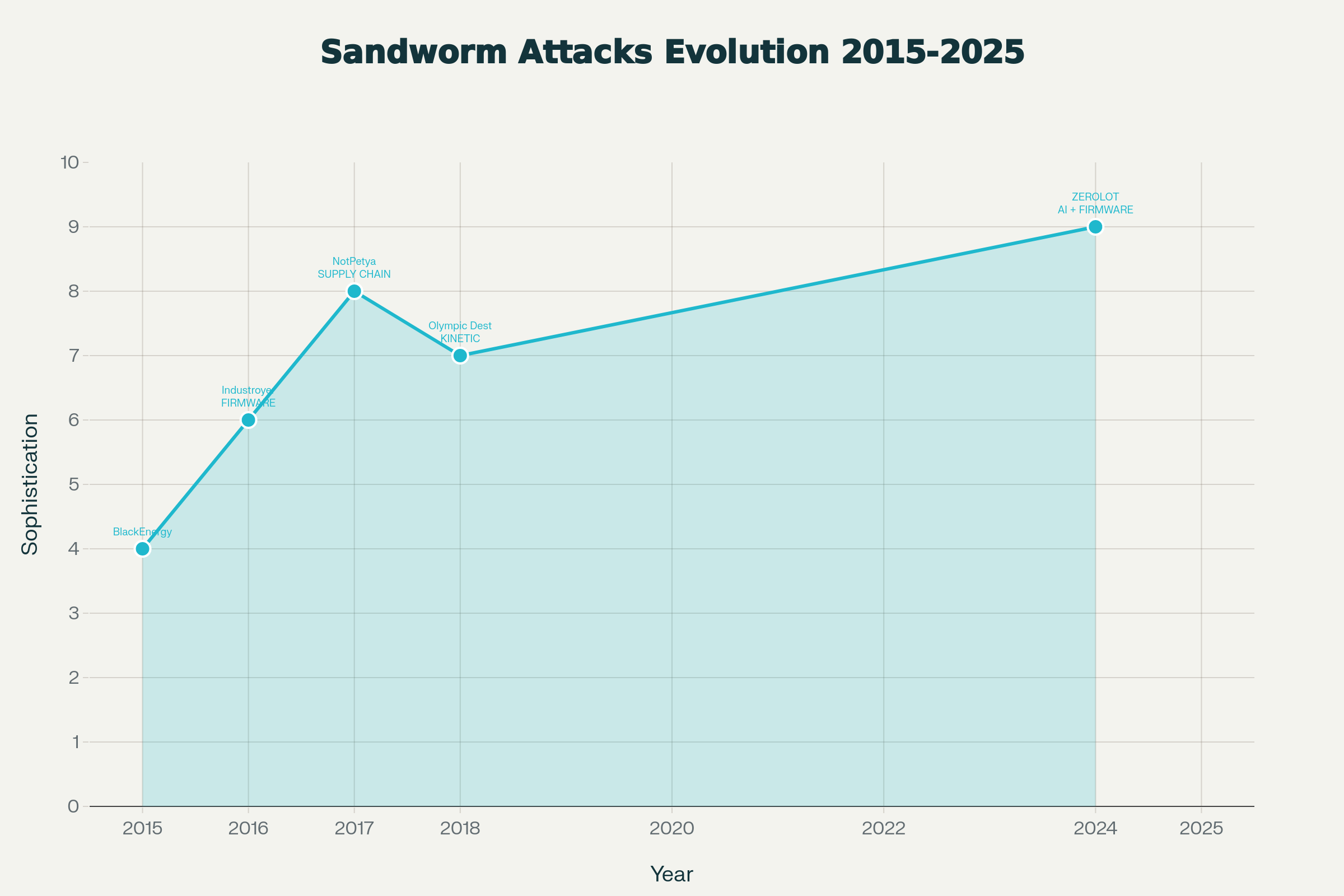
The Sandworm Evolution: From Espionage to Sabotage to Kinetic War
Sandworm (tracked as APT44, UAC-0145) represents the apex of state-sponsored destructive cyber capability. A decade-long trajectory shows evolution from espionage toward pure sabotage and kinetic integration:
2015 – BlackEnergy Attack: Sandworm compromised three Ukrainian power distribution companies via spear-phishing, laterally moved through networks for months, then executed a coordinated attack lasting 10 minutes that cut power to 230,000 customers. The malware used (KillDisk) was specifically designed to prevent operators from restoring power by wiping system disks and corrupting firmware.
2016 – Industroyer Attack: This represents a technical leap. Industroyer was the first malware specifically engineered to interface directly with industrial control system (ICS) protocols used in electrical substations. Rather than compromising human-machine interfaces (HMIs), Industroyer bypassed them entirely, communicating directly with relay protection systems and programmable logic controllers.
2017 – NotPetya Attack: Marketed as ransomware but actually a wiper, NotPetya spread globally via compromised software supply chains (Ukrainian accounting software) and caused over $10 billion in losses worldwide. The attack demonstrated Sandworm’s ability to compromise not just defense networks but civilian infrastructure at scale.
2018-2020 – Olympic Destroyer and Beyond: During the PyeongChang Winter Olympics, Sandworm disrupted Wi-Fi, ticketing, and broadcast systems—proof that cyber attacks could be coordinated with major geopolitical events for maximum impact.
2023-2025 – Firmware Persistence and Supply Chain: Sandworm’s latest tools (Cyclops Blink botnet, ZEROLOT wiper, SwiftSlicer) operate at firmware level, establishing persistence that survives operating system resets and factory resets. The group is now integrating with supply chains, compromising solar inverter manufacturers (SUN:DOWN research found 50+ vulnerabilities in Sungrow/SMA/Growatt systems with CVSS 9.8-10) to pre-position destructive access in power grid distributed generation systems.
The Technical Vulnerability: Why Power Grids Are Catastrophically Insecure
The Architecture Problem: Legacy Systems + New Interconnection
Modern power grids face a fundamental design flaw: They integrate ancient control systems with modern IT networks, creating vectors that legacy security frameworks never anticipated.
SCADA/ICS Inherent Risks:
- SCADA systems (Supervisory Control and Data Acquisition) were designed in the 1980s-1990s for closed networks with trusted operators. They assume security through obscurity, not cryptographic protection
- Many SCADA devices lack basic authentication mechanisms; some accept commands from any source on the network
- Firmware updates often cannot be deployed remotely, requiring physical access to substations—impractical at scale
- Hard-coded credentials embedded in firmware persist for years despite known vulnerabilities
Network Segmentation Failures:
- “Air-gap” isolation between IT networks (internet-connected, for business operations) and OT networks (isolated, for physical control) has largely disappeared
- Remote access for maintenance and monitoring—necessary for modern grid operations—creates inbound vectors from internet-facing systems to control networks
- Zero-trust architecture adoption remains nascent; most utilities operate on “trust but verify” assumptions that fail against sophisticated state actors
Detection & Response Gaps:
- Average dwell time (time from initial compromise to detection) exceeds 200 days for most organizations
Cyber Power Grid Attack Kill Chain: Stages, Detection Difficulty, and Timeline
- Most utilities cannot detect lateral movement within OT networks until damage occurs
- Incident response procedures were designed for ransomware and data theft, not coordinated infrastructure destruction
The Vulnerability Landscape in 2025
Known Critical Vulnerabilities (CISA advisories, 2025):
| System | Vulnerability Count | Max CVSS Score | Type | Exploitability |
|---|---|---|---|---|
| SunPower PVS6 Inverters | Multiple | 9.8 | Authentication bypass → grid control | Trivial (HTTP parameter manipulation) |
| Sungrow Inverters | 13 critical | 10.0 | Remote code execution → full control | Easy (network access) |
| GrowATT Inverters | 9+ critical | 9.9 | Unauthenticated firmware updates | Easy (no auth required) |
| ICS Protocols (IEC 61850) | Legacy | 9.2-10 | Unencrypted command execution | Moderate (network access) |
| Remote Access Tools | Ongoing | 9.5+ | Privilege escalation, persistence | Easy (credential theft) |
Sources: CISA 2025 advisories, Forescout SUN:DOWN research
Why These Matter: Solar inverters and distributed generation systems are increasingly integrated into grid operations for renewable energy management. A compromise affecting thousands of inverters across a region could create a coordinated botnet capable of destabilizing frequency, voltage, or synchronization across an entire grid.
The Dwell Time Reality: Attacks Are Likely Already Underway
Stage 1-4 (Reconnaissance Through Staging) = Probably Happening Now
The technical evidence suggests that sophisticated nation-state actors have likely already completed reconnaissance and initial access phases against NATO and U.S. power grids.
Evidence Supporting Active Pre-Positioning:
- ODNI 2025 Assessment explicitly states: “If Beijing believed that a major conflict with Washington was imminent, it could consider aggressive cyber operations against U.S. critical infrastructure… Such strikes would be designed to deter U.S. military action by impeding decision-making, inducing societal panic, and interfering with deployment of U.S. forces”
- Russian capability explicitly referenced: “Russia has demonstrated real-world disruptive capabilities during the past decade, including gaining experience in attack execution by relentlessly targeting Ukraine’s networks… its repeated success compromising sensitive targets for intelligence collection, and its past attempts to pre-position access on U.S. critical infrastructure make it a persistent counterintelligence and cyber attack threat”
- NATO cyber alerts escalating: NATO’s December 2025 statement confirmed Russia “is conducting cyberattacks” against NATO members, with hybrid threat operations below conventional warfare thresholds
- Infrastructure compromise confirmed: Multiple Baltic Sea incidents involved Russian vessels damaging undersea communication and power cables (11 incidents recorded, likely intentional “dragging anchor” operations to cause damage while maintaining deniability)
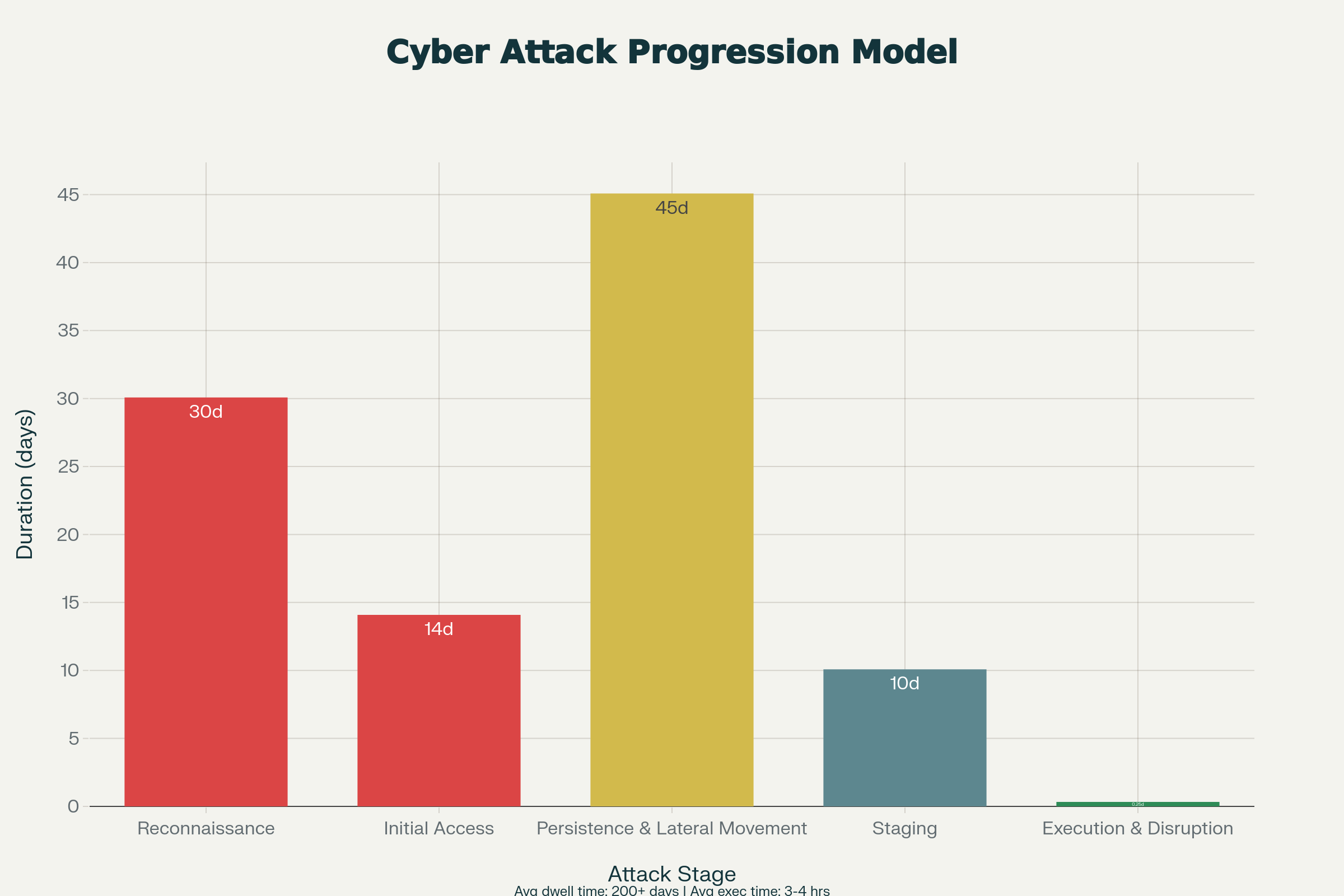
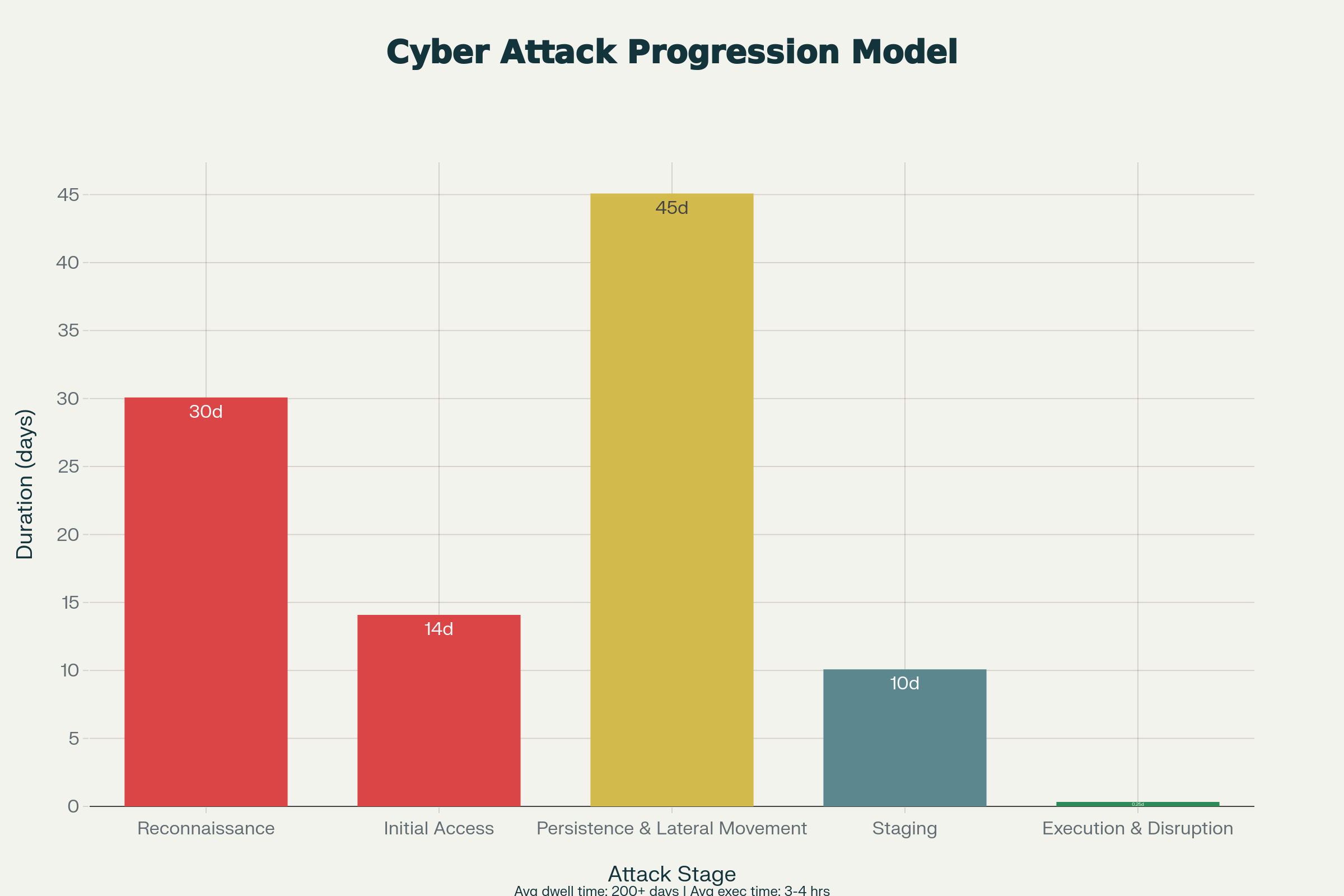
The Attack Progression Model: What the Kill Chain Actually Looks Like
Stage 1: Reconnaissance (30 days average)
- Attackers map network topology, identify SCADA devices, scan for vulnerabilities
- Detection difficulty: Hard (normal network activity can mask reconnaissance)
- Average detection delay: 60-90 days
- Entry vector: Often through utility employees’ personal networks, contractors, supply chain partners
Stage 2: Initial Access (14 days average)
- Compromise of contractor accounts, spear-phishing targeting utility employees, exploitation of unpatched zero-day vulnerabilities
- Detection difficulty: Hard (phishing and credential theft difficult to distinguish from normal activity)
- Average detection delay: 30-60 days
- Likelihood: Nearly 100% for sophisticated attackers against utilities with 500+ employees
Stage 3: Persistence & Lateral Movement (45 days average)
- Installation of backdoors, credential harvesting, movement from IT network to OT network
- This is where Ukrainian utilities should have detected attacks, but largely failed to
- Average detection delay: 20-40 days
- Duration extended deliberately to avoid triggering defenses
Stage 4: Staging (10 days average)
- Placement of destructive malware on target systems, final ICS reconnaissance, command-and-control infrastructure setup
- Detection difficulty: Medium (staging can sometimes be detected through anomalous traffic patterns)
- Average detection delay: 5-10 days
- This stage represents “point of no return”—malware is now on grid control systems
Stage 5: Execution (4 hours maximum)
- Remote command execution on SCADA systems, immediate effect on power generation/distribution
- Detection difficulty: Easy (alarms trigger immediately)
- But at this point, damage is already occurring
- Recovery time: 24-72 hours for grid stabilization (if no catastrophic equipment damage)
Total Average Dwell Time: 200+ days from initial access to detectable attack execution
Why Early Detection Fails
The Ukraine experience demonstrates the detection failure pattern:
- Utilities assume traditional IT security applies to OT networks: They focus on firewalls and antivirus, missing the fact that sophisticated attackers disable these during staging phase
- Lateral movement detection absent: Most utilities cannot detect when attackers move from IT networks (business operations) to OT networks (grid control). Ukrainian utilities had firewalls between the networks but lacked intrusion detection and logging
- Credential theft normalcy: Stolen credentials for legitimate accounts appear as normal login activity; defenders cannot distinguish legitimate access from compromised access without multi-factor authentication (rare in SCADA environments)
- Supply chain blindness: Utilities have limited visibility into contractors and vendors accessing their networks; Sandworm exploits this by compromising contractor environments and using them as staging areas
NATO’s Escalation Dilemma: The Article 5 Ambiguity
The Undefined Threshold Problem
NATO officially recognizes that cyber attacks “might in certain circumstances be considered an armed attack that could lead the North Atlantic Council to invoke Article 5″—but “certain circumstances” remains undefined.
Current Status of NATO Doctrine (December 2025):
- No public threshold defined for when cyber triggers Article 5
- Previous discussions have suggested “massive cyberattacks” could qualify, but “massive” is not defined
- German intelligence chief Bruno Kahl suggested that “continued sabotage could trigger Article 5,” but this remains speculation
- NATO maintains case-by-case analysis approach, meaning decisions occur during crises when time pressure distorts judgment
What Might Trigger Article 5?
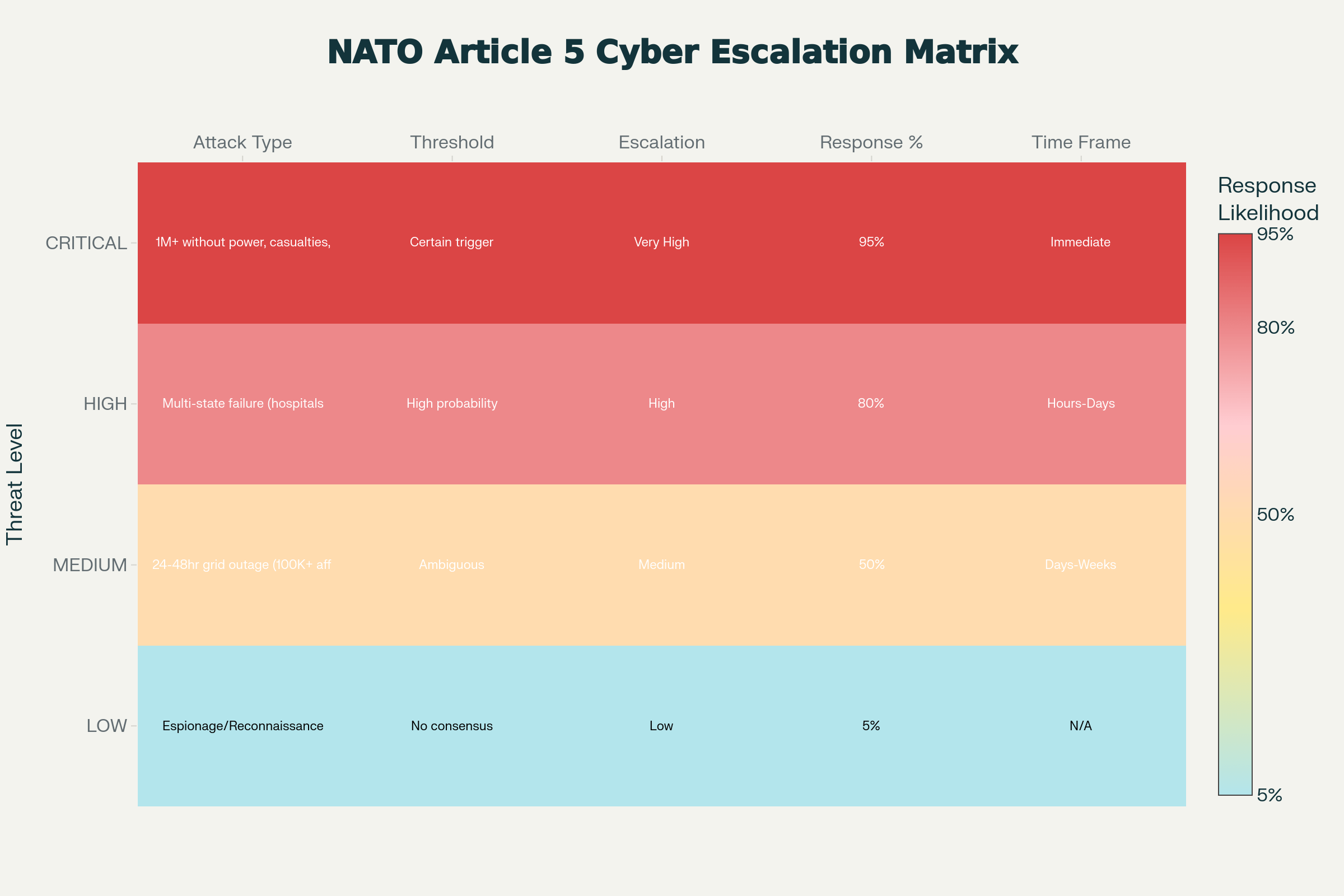
NATO Article 5 Cyber Threshold Matrix: The Ambiguous Escalation Landscape
Based on 2025 NATO discussions and Tallinn Manual guidance, the following scenarios could potentially invoke Article 5:
Definitely Would Trigger:
- Multi-state power grid failure affecting 10+ million people
- Power grid attack combined with cyber operations against military command-and-control systems
- Attack causing mass civilian casualties (hospital power loss, medical device disruption)
- Coordinated infrastructure attacks across multiple NATO members simultaneously
Probably Would Trigger:
- 48-72 hour national-scale grid outage affecting 5+ million people
- Attack on critical infrastructure (hospitals, water treatment, telecommunications) causing observable civilian harm
- Attack explicitly claimed by nation-state or clearly attributed via technical forensics
Ambiguous (Below threshold):
- 24-hour localized outages (<1M affected)
- Attack without claimed attribution or clear technical fingerprints
- Espionage-grade operations (data theft without destructive effect)
- Ransomware attacks (even if large-scale) that do not cause immediate physical damage
Current NATO Position (Post-December 2025 statements): NATO emphasizes it is “studying everything” regarding potential pre-emptive action and is considering more “aggressive” postures, suggesting uncertainty about whether to respond within traditional escalation frameworks or move toward forward defense.
The Escalation Risk
The ambiguity creates a dangerous dynamic:
Russian/Chinese Strategic Calculation: Both nations may believe they can conduct “sub-threshold” cyber attacks that cause significant damage without triggering Article 5—a miscalculation could escalate directly to nuclear conflict if NATO decides the attack was indeed an “armed attack”.
NATO Internal Division: With 32 member states required for Article 5 consensus, obtaining agreement that a cyber attack constitutes an “armed attack” during an active crisis is uncertain. Hungary, Turkey, or other nations could potentially block consensus, creating political chaos during a security emergency.
Pre-Emptive Strike Dilemma: NATO Admiral Giuseppe Cavo Dragone stated NATO is considering “pre-emptive” cyber action against Russia—but who defines what is “pre-emptive” when no official attack has occurred? This could justify NATO escalating to cyber offensive operations before any Russian action, creating a first-strike dynamic.
Scenario Analysis: Three Paths to the First Cyber World War
Scenario 1: The Controlled Incident (Probability: 25%)
Conditions: A significant but limited cyber attack occurs; attribution is rapid and certain; NATO responds proportionally through cyber channels; escalation control mechanisms hold.
What Triggers It:
- Russia conducts cyber attack on German or Polish power grid, affecting 2-3 million people for 24-48 hours
- Attack is clearly attributable to Sandworm (fingerprints obvious)
- Germany activates EU/NATO consultations
- NATO responds with cyber counter-operations against Russian military networks
Outcome:
- Escalation stops at cyber domain; no military kinetic response
- Both sides declare “demonstration of capability” completed
- New deterrence framework negotiated
- But underlying vulnerabilities remain
Why This Might Happen: If attackers are careful to limit civilian harm and leave clear attribution markers, NATO faces pressure to respond proportionally without escalating to kinetic conflict over a power outage.
Scenario 2: The Miscalculation Escalation (Probability: 40%)
Conditions: Cyber attack causes cascading failures beyond attacker’s calculation; NATO interprets damage as exceeding Article 5 threshold; Political divisions prevent consensus, leading to unilateral action.
What Triggers It:
- Russia targets power grid, expecting 24-hour outage
- Due to poor understanding of modern grids, outage cascades to 15+ million people across multiple countries
- Hospitals lose power (some patient deaths result), water treatment fails, communications disrupted
- NATO invokes Article 5; Russia denies attribution; technical evidence is ambiguous enough for Russia to claim false flag
Escalation Path:
- NATO conducts military cyber strikes on Russian military networks (acceptable under Article 5)
- Russia responds with counter-cyber operations against NATO military networks
- Both sides move to kinetic operations (air/missile strikes on each other’s cyber infrastructure)
- Rapid escalation to conventional war
Outcome: Potential WMD employment if either side believes it’s losing conventional exchange.
Scenario 3: Coordinated Multi-Vector Attack (Probability: 35%)
Conditions: Cyber attack on power grids coordinated with kinetic operations (drones, missiles, hybrid warfare); NATO cannot determine if cyber preceded kinetic or vice versa; Attribution becomes academic.
What Triggers It:
- Russia coordinates cyber attack on Baltic NATO power grids with simultaneous drone/missile strikes on same infrastructure
- Grid collapse + kinetic destruction creates dual layer of damage and confusion
- Confusion about attack source (cyber vs. kinetic) delays response
- NATO interprets dual-layer attack as escalation to kinetic warfare, invokes Article 5
Outcome: Full Article 5 response; potential NATO military action against Russian territory; rapid escalation potential.
Evidence Supporting: Amazon’s November 2025 threat report explicitly documented nation-state actors “bridging cyber and kinetic warfare,” with reconnaissance and cyber operations supporting kinetic targeting.
These scenarios depend on decisions made during crisis conditions when information is incomplete. For tracking NATO doctrine evolution, [subscribe to our defense intelligence updates].
What Defender Success Looks Like (And Why It’s Rare)
Ukraine’s Defense Model: Lessons from the Lab
Despite 1,000+ Russian cyber attacks and coordinated kinetic strikes, Ukraine’s power grid remains operational (severely damaged, but functioning). This provides the only available data on successful cyber defense at scale:
What Ukraine Did Right:
- Diversity: Multiple generation sources (hydro, thermal, nuclear) prevented single-point failures
- Manual Override Capability: Operators trained to operate systems manually when automated controls fail
- Rapid Recovery Procedures: Pre-planned system isolation and restoration procedures reduced recovery time
- Off-grid Backups: Critical facilities (hospitals, water treatment) with independent power systems survived grid collapse
- Personnel Readiness: Continuous training of operators on attack procedures and response
What Ukraine Couldn’t Prevent:
- Cascading Damage: Despite mitigation, coordinated attacks still damaged infrastructure faster than repairs could keep pace
- Economic Impact: The psychological/economic effect of threats to power reliability (even if mitigated) caused business paralysis
- Persistent Targeting: Russian attackers learn from each failed attempt and adapt tactics for next attack
Conclusion: Ukraine’s defense was reasonably successful at preventing catastrophic failures, but at the cost of accepting regular outages and economic disruption. NATO Europe is less prepared than Ukraine.
NATO’s Defense Gaps
Critical Missing Elements:
- ICS Segmentation: Many European utilities still cannot reliably isolate OT networks from IT networks
- Detection Capability: Only 15-20% of NATO utilities have network monitoring that would detect lateral movement within 30 days (Ukraine’s experience)
- Incident Response Plans: Most utilities have data breach response procedures, not infrastructure destruction procedures
- Mutual Aid Frameworks: No agreed framework for cross-border power assistance if one nation’s grid is compromised
- Offensive Capabilities: NATO countries have no established doctrine for offensive cyber retaliation, creating ambiguity about consequences
- Attribution Standards: No agreed technical standards for what constitutes sufficient attribution to justify cyber/military response
The Honest Assessment: The War Likely Starts Cyber
After examining the technical realities, threat actor capabilities, and NATO’s defensive posture, one conclusion emerges with high confidence:
If a major power conflict occurs, it will almost certainly begin with cyber operations against power grids and critical infrastructure. Not because cyber is the most destructive domain, but because it offers the attacker the best combination of:
- Deniability (at least for 24-48 hours)
- Psychological impact (mass blackouts terrify populations)
- Military advantage (power outage disables communications, complicates force deployment)
- Escalation control (can be calibrated to cause damage short of mass casualties)
Russia and China have demonstrated the capability. Sandworm’s Ukraine operations provide proof of concept. ODNI explicitly warns both nations could employ such tactics. The technical vulnerabilities are not theoretical—they are documented with CVE numbers and CVSS scores exceeding 9.8.
NATO’s defensive posture is inadequate. Not due to lack of effort, but due to the sheer technical difficulty of securing systems designed in the 1980s and interconnected with modern networks. Even Ukraine, battle-hardened and NATO-supported, cannot prevent power disruptions; it can only mitigate their duration.
The escalation threshold ambiguity creates additional risk. NATO’s undefined Article 5 cyber threshold means a cyber attack could trigger military escalation unexpectedly. Alternatively, NATO’s hesitation could signal weakness, encouraging Russian/Chinese aggression. Either way, the ambiguity is destabilizing.
What might challenge this view: Effective deterrence through NATO’s implicit threat of military response could prevent cyber attacks from occurring. However, Russia’s continued aggression in Ukraine despite NATO support suggests deterrence is not working; escalation is occurring anyway.
Implications and What to Watch
Near-Term Indicators (Next 6 Months)
NATO’s will move toward defined thresholds: Will NATO publish explicit guidance on when cyber triggers Article 5? Publication would clarify deterrence but could also signal escalation readiness.
European utility hardening acceleration: Watch for announcements on ICS segmentation projects, network monitoring upgrades, and mutual aid frameworks.
Russian/Chinese cyber signaling: Will either nation conduct provocative cyber operations designed to test NATO’s response? (Both have track record of testing boundaries)
Sandworm activity levels: Increased reconnaissance activity against NATO infrastructure would suggest preparation for major operations.
Medium-Term (6-24 Months)
Doctrine maturation: NATO likely to formalize cyber defense roles and offensive response options.
Capability development: Expect announcement of NATO-level cyber response units and offensive capabilities.
Vulnerability remediation pace: Will utilities actually patch critical ICS vulnerabilities, or will legacy systems remain exposed?
Pre-emptive action consideration: Will NATO move from defensive to proactive/pre-emptive posture? NATO Admiral Cavo Dragone’s December 2025 suggestion of pre-emptive strikes could evolve into doctrine.
Long-Term Strategic Shift (24+ Months)
Cyber as domain of first contact: Both NATO and Russia/China may come to view cyber as the appropriate domain for initial conflict operations, treating it as less escalatory than kinetic warfare.
Escalation ladders vs. lattices: Will NATO develop clear escalation frameworks, or will cyber remain in the ambiguous gray zone where misunderstandings trigger unintended escalation?
Technology evolution: Will emerging AI-driven cyber defense (anomaly detection, automated response) actually improve security, or will AI-enabled attacks evolve faster than defenses?
Stay Informed: Defense Intelligence That Matters
Power grid cyber warfare represents one of the most consequential and least understood risks facing NATO and the broader international system. The technical capabilities exist, the threat actors are prepared, and vulnerabilities persist.
Subscribe for ongoing analysis that:
- Tracks NATO doctrine evolution on cyber Article 5 thresholds
- Monitors Sandworm and other state-sponsored group activity levels
- Analyzes utility vulnerability remediation progress (or lack thereof)
- Provides frameworks for understanding escalation risk in cyber domain
- Covers emerging defensive and offensive technologies
Join our community of defense professionals and critical infrastructure stakeholders.
For daily insights on cyber warfare developments and real-time threat tracking, follow X (Twitter): @trends91blog.
For professional analysis and infrastructure security implications, connect on LinkedIn: Trends91.
For comprehensive intelligence delivered directly, Subscribe Here.
Join strategists and security professionals who monitor emerging threats.
📈 About This Analysis & The Author
This analysis follows the Trends91 Unrestricted Framework, prioritizing evidence-based threat assessment, multiple scenario consideration, and acknowledgment of genuine strategic uncertainties.
Key Sources Referenced:
- ODNI 2025 Threat Assessment – Official U.S. intelligence assessment of cyber threats
- NATO Official Statements – December 2025 cyber policy and escalation doctrine
- AWS Threat Intelligence – Nation-state cyber-kinetic bridging evidence
- Ukrainian Power Grid Data – Combat-proven attack and defense evidence
- Sandworm/APT44 Analysis – MITRE ATT&CK, academic research, threat reports
- CISA ICS Advisories – Critical infrastructure vulnerability data
- NATO Cyber Defense Centre – Escalation doctrine and threshold analysis
- Academic Research – Zero-day exploits, escalation ladders vs. lattices
For real-time updates on cyber operations and emerging threats, follow X (Twitter): @trends91blog.
For strategic analysis and defense implications, connect on LinkedIn: Trends91.
Engagement drives better analysis. Have intelligence assessments, updated threat data, or alternative scenarios? Reach out on either platform.

